The 2020 COVID pandemic forced businesses to double down on their digital investments as in-person moved online. Brands refined and upped their marketing investments across digital channels - email, websites, social media, apps, and advertising - to serve their customers along their digital buying journeys. And while we were all focusing on managing life in the face of these shifts, malicious actors demonstrated once again that they are quick studies as they increased their investment in these same digital channels to promote their illicit activities on the strength of famous brands.
These highly-organized bad actors modeled their abuse networks by infringing upon the trademarks, brand names, hashtags, slogans, and even web page text used by the brands they target. To weave their schemes, they used the same promotional vehicles and digital assets as the targeted brands we all love. They built websites and apps, registered related URLs, social profiles, and pages to promote themselves. And in the case of counterfeit and grey-market goods, they created seller profiles and marketplace listings.
In short, economically-motivated bad actors apply modern digital marketing strategies and technology to conduct systemic brand abuse and take advantage of consumers using the most loved brands as bait.
These sophisticated abuse networks appear ‘friendly’ to their victims, often including customer service chat and bots. Bad actors even take advantage of the latest advances in Martech (marketing technology) to conduct powerful customer - or more accurately, victim - acquisition strategies, using tracking pixels on their web pages and ‘retargeting’ ads across the web to reinforce their messages.
In short, economically-motivated bad actors apply modern digital marketing strategies and technology to conduct systemic brand abuse and take advantage of consumers using the most loved brands as bait.
To understand the scope of systemic brand abuse, the Appdetex team used our patent-pending Appdetex Tracer™ technology to profile these highly-organized networks of bad actors.
How big is the problem?
On average:
- Abuse is systemic. 25% of abuse is part of a systemic abuse network.
- Abuse networks grow significantly. Over a six-month period, unabated abuse network connections, or Traces, increased by 30% while the number of network nodes grew by nearly 10X.
- App and domain nodes are most likely connection points. 47% of confirmed abusive apps have related nodes. 27% of abusive domain names are related to other abuse.
- Content and Social media provide important indicators of abuse. 14% of websites that did not include infringement in the domain name were related to malicious activity, while 9% of abusive social handles and profiles were related to additional instances of abuse.
Systemic Abuse By Channel
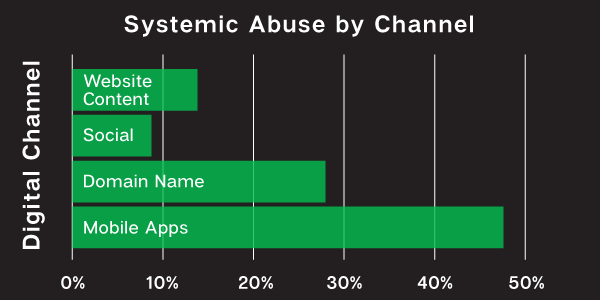
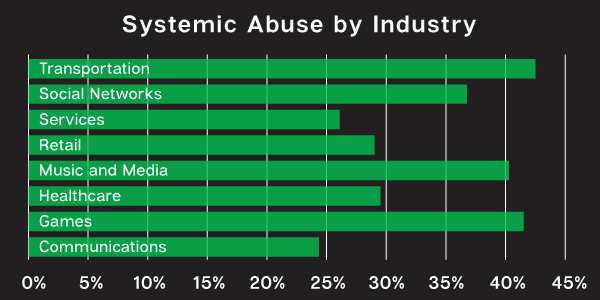
We examined a variety of industries, too, and found that, while no sector was immune, the highest incidence of abuse occurred in gaming, music and media, social networks, and, surprisingly, transportation industries. With the rise of COVID, consumers have increasingly relied upon delivery services, making the transportation category a larger target for bad actors.
Systemic Abuse by Industry
What does this mean for brand enforcement professionals?
The advent of domain name privacy and proxy services as well as privacy regulation and technologies have had the unintended consequence of enabling bad actors to hide their identities. As malicious actors learned how they are being tracked, they began using multiple obfuscation layers to make it harder to find their operations and dismantle them.
To solve this problem, we developed Appdetex Tracer. This patent-pending investigative technology uses advanced crawling, scraping, and automated analytics tools to find the unseen digital links between sites, ads, listings, social networking handles, and apps used by these sophisticated networks of bad actors. These links, or Traces, can be as simple as publicly available domain registration data or as subtle as the security, customer service, or marketing and customer service technology providing the criminal network’s infrastructure.
Traces link the individual elements of a brand abuse gambit whether those elements are a marketplace listing, a website, a social media profile, an ad, or an app. We refer to these elements as nodes.
Why is knowing which abuse is part of a network important?
Traditional brand protection technologies rely on scanning to identify the nodes of a network, and they exclude the linkages and discovery of related abuse. As a result, brand protection professionals who use these legacy technologies are able to pursue enforcement for the individual nodes but are unable to identify related abuse, leaving large swaths of criminal operations in place and continuing to profit from the targeted brand. A considerable proportion of these unidentified nodes are part of a criminal network, and these networks are often very damaging to brands over long periods.
How to Combat Systemic Abuse
- Use automated investigation solutions to uncover large criminal digital networks. Understanding the traces, finding the nodes of a network, mapping the criminal activity, using offline sources to augment traces and connections, identifying the malicious individual or organization, and developing a strategy for stopping organized actors is an essential methodology for brand protection professionals to defend brands.
- Employ an abuse map and a strategy to stop organized malicious actors.
If you know your adversary, you can employ advanced techniques to disable malicious actors and dismantle their networks. These advanced techniques range from stopping payment processing capabilities to initiating a mass UDRP or even litigating. These activities have a higher chance of a successful outcome with the intelligence provided by automated intelligence and investigation solutions that document bad-actor networks. - Use individual enforcements to take down incidental abuse and more advanced means to stop malicious abuse networks.
Often abuse networks rely on unbranded infrastructure to monetize their schemes. Their apps, checkout pages, marketplace listings, and social commerce sites may have no branding whatsoever. So, dismantling the promotional network incrementally - one ad, social profile, marketplace listing, or domain at a time - doesn’t stop bad actors; it only slows them. The most sophisticated networks of bad actors can absorb slowdowns and re-create their infrastructure reasonably quickly, putting them back into targeting your business.
Methodology
Our survey findings are based on the confirmed abuse and resulting enforcement of more than 100,000 online infringement cases and instances of abuse over a one-year period. Among the industries included in the study were Music & Media, Transportation, Retail, Gaming, Communications, Healthcare, and others.
We used our patent-pending Appdetex Tracer technology to investigate these instances of infringement. With Appdetex Tracer, we were able to map the networks, document the connection points, or ‘traces,’ and identify additional network nodes. As a result, we were able to uncover additional related abuse networks targeting the industries in the study.
To find out more about modern brand protection, you can request a demo here.